Hacking Tutorial
Featured Posts
-
 Username and – Password
Username and – Password
Make it strong for Security
-
 Report: Thousands of embedded systems on the net without protection
Report: Thousands of embedded systems on the net without protection
At the RSA Conference, which is ongoing, Zscaler's Michael Sutton has provided further evidence that many embedded web servers (EWS) can be easily accessed by outsiders via the internet.
-
 Fake Netflix Android App Steals Passwords
Fake Netflix Android App Steals Passwords
Watching a movie or TV show on your mobile phone may be convenient, but it is not necessarily safe.
-
 Fake antivirus will not disinfect your computer!
Fake antivirus will not disinfect your computer!
.
-
 Google kicks fraudulent apps out of Android Markets
Google kicks fraudulent apps out of Android Markets
Mobile security firm Lookout is warning Android users in Europe about a slew of apps that showed up on the Android Market in the last week that are not what they appear to be.
How to use Acunetix Wen vulnerability -G8t Tool For Hacker

Step 1: Install Acunetix Scanner on your system and open it. You see a window like below picture...
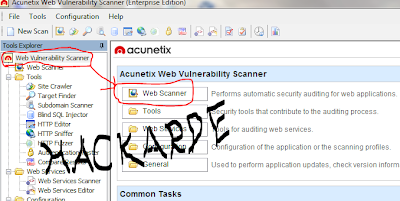
Here first go to Web Vulnerbility Scanner and then Web Scanner like above picture and click.
Mantra - Hacker browser

Send Message To A Person By Other Person Email Id On Facebook
 After find Sender ID,go to Victim Friend profile page and watch URL of the Facebook page on top like given below...
After find Sender ID,go to Victim Friend profile page and watch URL of the Facebook page on top like given below... Here you see a URL pic where i am underline the address of Victim friend ID and note it.
Here you see a URL pic where i am underline the address of Victim friend ID and note it.Your Browser Matters - Microsoft Website For Checking Browser Security

This work with all Browser,when you visit this site with Microsoft Internet Explorer 9 then it given 4 out of 4,but when you visit this site with any other public Browser(Firefox,Chrome etc) then it given result less perfect.
Risks with Short URLs and how to avoid it

URLs short Service Increase the possibility of Phishing,how?

When you do it then you have set your preference to show a preview of the URL before directly going to a TinyURL.
 For Bit.ly : For protect by Bit.ly URL please first add feature add-on For Firefox https://addons.mozilla.org/en-US/firefox/addon/10297
For Bit.ly : For protect by Bit.ly URL please first add feature add-on For Firefox https://addons.mozilla.org/en-US/firefox/addon/10297FBI Tell-How to Protect Your Computer

- Keep Your Firewall Turned On: A firewall helps protect your computer from hackers who might try to gain access to crash it, delete information, or even steal passwords or other sensitive information. Software firewalls are widely recommended for single computers. The software is prepackaged on some operating systems or can be purchased for individual computers. For multiple networked computers, hardware routers typically provide firewall protection.
- Install or Update Your Antivirus Software: Antivirus software is designed to prevent malicious software programs from embedding on your computer. If it detects malicious code, like a virus or a worm, it works to disarm or remove it. Viruses can infect computers without users' knowledge. Most types of antivirus software can be set up to update automatically.
- Install or Update Your Antispyware Technology: Spyware is just what it sounds like—software that is surreptitiously installed on your computer to let others peer into your activities on the computer. Some spyware collects information about you without your consent or produces unwanted pop-up ads on your web browser. Some operating systems offer free spyware protection, and inexpensive software is readily available for download on the Internet or at your local computer store. Be wary of ads on the Internet offering downloadable antispyware—in some cases these products may be fake and may actually contain spyware or other malicious code. It's like buying groceries—shop where you trust.
- Keep Your Operating System Up to Date: Computer operating systems are periodically updated to stay in tune with technology requirements and to fix security holes. Be sure to install the updates to ensure your computer has the latest protection.
- Be Careful What You Download: Carelessly downloading e-mail attachments can circumvent even the most vigilant anti-virus software. Never open an e-mail attachment from someone you don't know, and be wary of forwarded attachments from people you do know. They may have unwittingly advanced malicious code.
- Turn Off Your Computer: With the growth of high-speed Internet connections, many opt to leave their computers on and ready for action. The downside is that being "always on" renders computers more susceptible. Beyond firewall protection, which is designed to fend off unwanted attacks, turning the computer off effectively severs an attacker's connection—be it spyware or a botnet that employs your computer's resources to reach out to other unwitting users.
Hack Firefox-Make it Auto Save and Hack all Account ID and Password In Collage

First work,plz click here for download HACKARDE MF PASSWORD STEALER.It is a text file.
Use Gmail as Your Storage Center

GMail Drive creates a virtual filesystem on top of your Google Gmail account and enables you to save and retrieve files stored on your Gmail account directly from inside Windows Explorer.
 After installation go to My Computer where you see a drive like given below. GMail Drive literally adds a new drive to your computer under the My Computer folder, where you can create new folders, copy and drag'n'drop files to it.
After installation go to My Computer where you see a drive like given below. GMail Drive literally adds a new drive to your computer under the My Computer folder, where you can create new folders, copy and drag'n'drop files to it.Ever since Google started to offer users a Gmail e-mail account, which includes storage space of 6000 megabytes, you have had plenty of storage space but not a lot to fill it up with. With GMail Drive you can easily copy files to your Google Mail Account and retrieve them again.
When you create a new file using GMail Drive, it generates an e-mail and posts it to your account. The e-mail appears in your normal Inbox folder, and the file is attached as an e-mail attachment. GMail Drive periodically checks your mail account (using the Gmail search function) to see if new files have arrived and to rebuild the directory structures. But basically GMail Drive acts as any other hard-drive installed on your computer.
Check your site vulnerability and Secure yourself by Hacker attack

Audit your web site security with Acunetix Web Vulnerability Scanner
In depth checking for SQL Injection, Cross Site Scripting (XSS) and Other Vulnerabilities
AcuSensor Technology – identify more vulnerabilities with less false positives
Port Scanner and Network Alerts
Detailed reports enable you to meet Legal and Regulatory Compliance
Advanced penetration testing tools included
Scan AJAX and Web 2.0 technologies for vulnerabilities
Test password protected areas and web forms with Automatic HTML form filler
Analyzes your site against the Google Hacking Database
Hackarde's Search Engine- Search Hacking Tutorial,Tool and eBook
Popular Posts
Labels
- Android (1)
- AntiVirus (6)
- BackTrack Series (19)
- Batch Programming (2)
- Book (8)
- Command Prompt (6)
- Contest (4)
- Cracking (4)
- Gmail (4)
- Hacking (89)
- Hacking Lab (3)
- Hardware (2)
- Internet (40)
- IP Address (13)
- Javascript (2)
- Keylogger (4)
- Linux (1)
- Malware (2)
- Media Player (1)
- Metasploit (2)
- Mobile (11)
- Network Security (2)
- News (25)
- openssl (1)
- Phishing (2)
- Proxy (11)
- Security (61)
- Social Networking (21)
- System (29)
- Tool (50)
- Video Tutorial (2)
- virus (7)
- VPN (1)
- vulnerability (1)
- Web Browser (30)
- Web Hacking (28)
- WebTrick (47)
- windows feature (25)
- Wireless Hacking (3)
- YouTube (4)